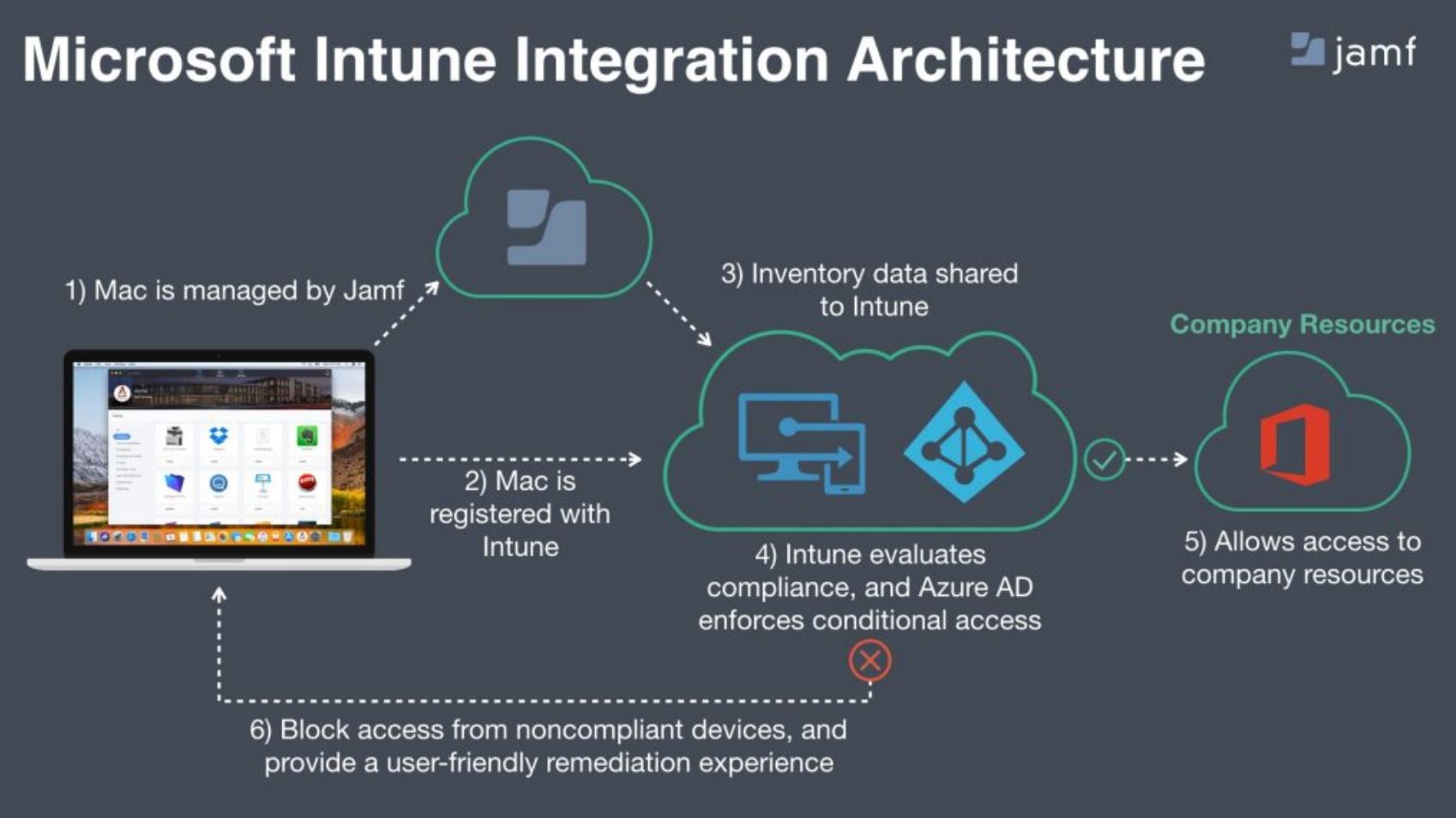
Intune For Mac
Microsoft Intune supports the deployment of applications using InstallApplication. This opens the possibility to manage Mac computers with Microsoft Intune, and automatically push Munki to provide additional functionality.

The process for that is outlined in How to add macOS line-of-business (LOB) apps to Microsoft Intune
Microsoft Intune supports the deployment of applications using InstallApplication. This opens the possibility to manage Mac computers with Microsoft Intune, and automatically push Munki to provide additional functionality. The process for that is outlined in How to add macOS line-of-business (L. Manage OS Updates via Intune. I've read that MacOS (and also iOS) will get the ability to update to a specific OS-version via the MDM-channel if I understand correctly (iOS 12, Mac OS 10.14), does anyone know if this function will be available to do from Intune? Today you can set minimum or maximum OS-version for Mac viaM365 CA5 but that's not.
Make sure:
Your packages are “distribution packages” and signed with a “Developer ID Installer” certificate. See distributing packages with InstallApplication and Intro to installing macOS content from a web server
They don’t contain a space in their filename (thanks, @emilp333!)
As far as I know, there’s no way to make these macOS LOB apps to be installed during the setup assistant (also called: “Bootstrap package”. In practice, the delay between enrolment and the app being deployed can be quite long (I’ve seen 5 minutes while clicking on “Sync” frantically). Also, Microsoft Intune seem to be a little slow to report success or failure in the console. Perhaps time for a User voice feedback?
As the power of Microsoft Intune grows with great force, in this blog post we are going to look at how to install Google Chrome and manage via Microsoft Intune. I have been recently looking how to leverage Microsoft Intune for more than just Microsoft based tooling and Google Chrome can be installed and managed for Windows 10 desktop estate.
Installing Google Chrome
Download Google Chrome Package
Visit the following url to download Google Chrome for Enterprise
https://cloud.google.com/chrome-enterprise/browser/download/
Microsoft Intune
First of all, we need to log into your Azure Portal and go to the following location;
- Microsoft Intune
- Client Apps
- Add
- Line-of-business app
Now we need to select the GoogleChromeStandaloneEnterprise msi located within the zip file package

You will now need to populate a bit of information under App information field below App package files before being able to assign Google Chrome to all your enterprise or selected security groups.
As you can see from the image below I have targeted several security groups within my personal tenant and make the app required for all users / all devices.
Make sure you save you configured as you exit this configuration.
Managing Google Chrome
Import Google Chrome ADMX Templates
- Download the Chrome ADMX templates.
- You would have already completed this step when downloading the Google Chrome Msi.
- Sign in to the Microsoft Azure portal.
- Go to Intune Device configuration Profiles.
- Next to Devices configuration – Profiles, click Create
profile . - Enter the following text in these fields:
| Field | Text to enter |
| Name | Windows 10 – Chrome configuration (or use any descriptive name) |
| Description | Enter a description (optional) |
| Platform | Windows 10 and later |
| Profile type | Custom |
| Settings | Custom (select from drop-down list) |
Selecting Custom in the step above opens a new menu for OMA-URI settings. Click Add to add specific policies you can configure and enter the following text:
| Field | Text to enter |
| Name | Chrome ADMX Ingestion |
| Description | Enter a description (optional) |
| OMA-URI | /Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Chrome/Policy/ChromeAdmx |
| Data typeProfile type | String (select from |
- Once you select String, a Value text field opens below. On your computer, go to
- Copy the text from chrome.admx.
- In the Value field, paste the chrome
. text.admx - Click OK and OK again to save the Custom OMA-URI settings.
- Click Create to create a new profile.
Configure Google Chrome Policy
- Go to Intune –> Device Configuration –> Profile
- Click the Windows 10 – Chrome configuration profile you created
previous - Select Properties –> Settings –> Configure to open Custom OMA-URI setting
- Click Add to a row
- Enter text into the fields, following the examples below for the type of policy you’re implementing.
Example A: Disable Password Manager
| Field | Text to enter |
|---|---|
| Name | Chrome – ADMX – PasswordManagerEnabled |
| Description | Disable Password Manager |
| OMA-URI | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome~PasswordManager/PasswordManagerEnabled |
| Data type | String |
| Value |
Intune For Mac
List of all Google Chrome Configurations
The below tables provides all the settings that are available for delivery using Microsoft Intune
| Policy | OMA-URI | Data type | Example value |
| Chrome – ADMX – AllowOutdatedPlugins | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome/AllowOutdatedPlugins | string | <disabled/> |
| Chrome – ADMX – AudioCaptureAllowedUrls | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome/AudioCaptureAllowedUrls | string | <enabled/> <data id=”AudioCaptureAllowedUrlsDesc” value=”1[*.]example.com“/> |
| Chrome – ADMX – AutoFillEnabled | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome/AutoFillEnabled | string | <disabled/> |
| Chrome – ADMX – CloudPrintSubmitEnabled | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome/CloudPrintSubmitEnabled | string | <disabled/> |
| Chrome – ADMX – DefaultBrowserSettingEnabled | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome/DefaultBrowserSettingEnabled | string | <enabled/> |
| Chrome – ADMX – DefaultPopupsSetting | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome~ContentSettings/DefaultPopupsSetting | string | <enabled/> <data id=”DefaultPopupsSetting” value=”1″/> |
| Chrome – ADMX – DefaultSearchProviderEnabled | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome~DefaultSearchProvider/DefaultSearchProviderEnabled | string | <enabled/> |
| Chrome – ADMX – DefaultSearchProviderName | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome~DefaultSearchProvider/DefaultSearchProviderName | string | <enabled/> <data id=”DefaultSearchProviderName” value=”Google Encrypted Search”/> |
| Chrome – ADMX – DefaultSearchProviderSearchURL | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome~DefaultSearchProvider/DefaultSearchProviderSearchURL | string | <enabled/> <data id=”DefaultSearchProviderSearchURL” value=”https://www.google.com/search?q={searchTerms}”/> |
| Chrome – ADMX – DisableSafeBrowsingProceedAnyway | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome/DisableSafeBrowsingProceedAnyway | string | <enabled/> |
| Chrome – ADMX – ExtensionInstallForcelist | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome~Extensions/ExtensionInstallForcelist | string | <enabled/> <data id=”ExtensionInstallForcelistDesc” value=”1heildphpnddilhkemkielfhnkaagiabh;https://clients2.google.com/service/update2/crx”/> |
| Chrome – ADMX – ForceGoogleSafeSearch | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome/ForceGoogleSafeSearch | string | <enabled/> |
| Chrome – ADMX – ImportAutofillFormData | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome/ImportAutofillFormData | string | <disabled/> |
| Chrome – ADMX – ImportBookmarks | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome/ImportBookmarks | string | <enabled/> |
| Chrome – ADMX – ImportHistory | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome/ImportHistory | string | <disabled/> |
| Chrome – ADMX – ImportHomepage | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome/ImportHomepage | string | <enabled/> |
| Chrome – ADMX – ImportSavedPasswords | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome/ImportSavedPasswords | string | <disabled/> |
| Chrome – ADMX – ImportSearchEngine | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome/ImportSearchEngine | string | <disabled/> |
| Chrome – ADMX – NotificationsAllowedForUrls | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome~ContentSettings/NotificationsAllowedForUrls | string | <enabled/> <data id=”NotificationsAllowedForUrlsDesc” value=”1[*.]example.com“/> |
| Chrome – ADMX – PasswordManagerEnabled | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome~PasswordManager/PasswordManagerEnabled | string | <disabled/> |
| Chrome – ADMX – PluginsAllowedForUrls | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome~ContentSettings/PluginsAllowedForUrls | string | <enabled/> <data id=”PluginsAllowedForUrlsDesc” value=”1[*.]example1.com2[*.]example2.com“/> |
| Chrome – ADMX – SafeBrowsingEnabled | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome~SafeBrowsing/SafeBrowsingEnabled | string | <enabled/> |
| Chrome – ADMX – VideoCaptureAllowedUrls | ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome/VideoCaptureAllowedUrls | string | <enabled/> <data id=”VideoCaptureAllowedUrlsDesc” value=”1[*.]example.com“/> |
Intune For Macbooks
This concludes this post.
Regards,
The Author – Blogabout.Cloud
Intune For Mac Os Unable To Enroll
Related
